
UVK Help - Threat Scanner


This section can be accessed by pressing Threat Scanner in the Home page.
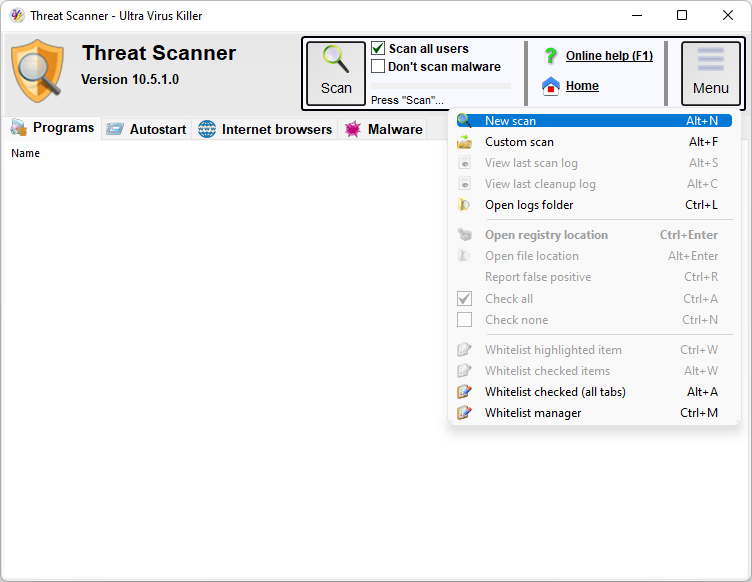
Threat Scanner's overview
UVK's Threat Scanner is a simple but powerful adware and malware remover for Windows, which has the ability to scan all the users in a system. This can save you lots of time logging in to other user accounts and performing the scan again.
Threat Scanner is also the only application of this type that supports nearly all Internet browsers, not just the main ones.it removes browser toolbars, ad-ons, plugins, unwanted search providers and hijacked home pages, potentially unwanted programs (PUP's), and also rogues, trojans, rootkits, ransomware and all other forms of malware. It also lets you optionally reset the browser settings, allowing them to run as smoothly as when they were installed. Click here for more info.
Most well known browsers are supported (Chrome, Edge, Firefox, IE). Support for other Chromium and Firefox based brosers was added in version 10.4 and 10.5. Opera, Avast Secure Browser, cCleaner Browser, Brave, Chromium, Tor Browser, Waterfox, Netscape and Thunderbird and many others are now supported, at least partially.
Threat Scanner was built to be fast, simple and effective. Usually you just need to press the Scan button, wait until the scan ends, and then remove the items found. Normally the whole operation takes only a few minutes. For more information, please see our help content.
Threat Scanner can also be downloaded as a separate portable app here.
Scanning for adware and malware
To start a scan, press the Scan button. This button is then renamed Stop. You can press it again anytime during the scan, to cancel the scan. The whole scan usually only takes a few minutes.
If you want to scan only the current user, uncheck Scan all users, before starting the scan. The SYSTEM user account will always be scanned, though.
The progress bar to the right the Scan button will tell you the scan's progress, and a text label below the progress bar will tell you which section is currently being scanned.
While the scan is being performed, you can have a look the the items already found. Double-clicking an item automatically takes you to its location in the registry. You can also jump to the item's location in the file system, when available, by right-clicking the item's line and selecting Open file location. This allows you to have a better insight of the item, and decide whether you want to remove it or not.
Tip: To save time, while the scan is being processed, uncheck any items you don't want to remove, or whitelist items you don't want Threat Scanner to display in future scans. More info on the whitelist below.
You can quickly check/unckeck all items in the list: right-click the list to open it's context menu, and then select Check all, or Check none, respectively. The context menu also has a Open registry location menu item which will perform the same action as double-clicking the list item, as mentioned above.
When the scan is complete you will be presented with a message box telling you how many items were found, and you can access the scan's log by pressing the Menu button, and then selecting the View scan log menu item.
Whitelist
As mentioned above, you can whitelist any of the items in the list, after a scan is complete, or even during the scan. Just select the desired list (Programs, Internet Explorer, Chrome or Firefox), then right-click the item you want to whitelist and finally select Whitelist this item. Whitelisted items will not be detected again and are immediately removed from the list.
To manage the Threat Scanner's whitelist, press the Menu button, and select Whitelist manager. You will be presented with a dialog box similar to the one in the picture below.
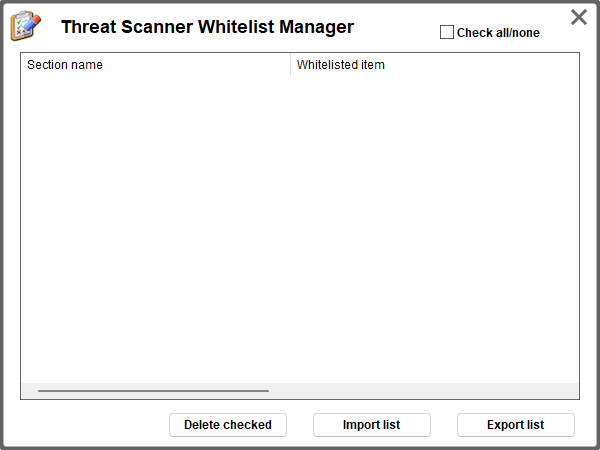
The list shows the whitelisted items. To remove items from the white list, tick the checkbox next to the items you want to remove, press Delete checked and confirm. This removes the item(s) form the whitelist, meaning they will be detected again, when detected.
You can easily export and import the whitelist to/from an external file. This will be particularly useful to make baclup copies of the whitelist, or to transfer it to a different computer.
To import the whitelist from a file, press Import list and select the INI file the list was previously exported to.
To export the list, press Export list and select the INI file path and name you wish to export to.
If you save the ini file in the same directory as UVKPortable or UVKSetup, and the INI file name is UAK_White_list.ini, the UVK package will automatically import the whitelist the next times you use it to install and run UVK.
When you are done using this feature, press Close / Cancel to close this dialog box.
Selecting the items to remove
Before removing the items found, you can set the check state of the items you want to remove, or ignore. Items will only be removed/fixed if the corresponding check box is ticked. Threat Scanner simplifies the selection process by providing only the names of the programs to remove, in the Programs list, and by spliting the browser repair options into several groups.
Threat Scanner automatically checks most of the items during the scan. However, some items may not be checked by defaut, depending on their nature. You can check the desired items in just a few seconds.
Browser reset options and malware related fixes are usualy unchecked. You can manually check those options if removing the other items did not restore the desired functionality. Try removing the items selected by default once, if that does not fix your problem, check all the options and try again. That should get your browsers and your system working properly.
After selecting the desired items to remove or fix, you are ready to begin the removal process.
Deleting/fixing the selected items
Once the scan is complete, and you selected the desired items to fix, press the Cleanup button to start removing or fixing the selected items.
Some of the selected items will be removed, but others will be fixed instead. For instance, hijacked browser shortcuts will be fixed, programs are always removed. Threat Scanner knows which items it must fix or delete, no action is required from your side.
If the Create restore point check boxis ticked, a system restore point is created before the removal process.
File system objects that Threat Scanner does not manage to remove immediately are scheduled for removal on reboot. In this case, Threat Scanner will ask you if you want to reboot immediately. You can choose No, if you want to manually reboot later.
Once the removal process is complete, you can read the removal log by pressing the Menu button and then selecting the View removal log menu item.
Application logs
You can access the scan and removal logs by pressing the Menu button and then selecting View scan log, or View removal log. Obviously, the scan log is only available after you complete a scan, and the removal log is only available after you remove the items found.
If you want to access logs of previous scans or removals, select Open logs folder, instead, and manually open the desired log. Application log names are timestamp based, meaning the higher the number in the log's file name, the more recently the log was created. The Windows file explorer should automatically sort them in the correct order, from the oldest to the newest.
The logs are very self-explanatory. The scan log contains a header with some useful system information, such as the Windows version, installed browsers versions, and the name of the user that started Threat Scanner.
Items found (in the scan log) or items removed (in the removal log) are ordered by the corresponding section: File objects, Registry, Services, Tasks, Shortcuts, Internet Explorer, Chrome and Firefox.
In the scan log, registry related items are prefixed in a special way, that makes easier to identify the corresponding registry key, and also shortens the line's text:
@UserName: A registry key located in the UserName's
registry portion (hive).
HKLM64: A registry key located in
the 64 bit portion of the HKEY_LOCAL_MACHINE key, in 64 bits Windows
versions.
HKLM32: A registry key located in the 32 bit
portion of the HKEY_LOCAL_MACHINE key, in 64 bits Windows versions.
HKCR64: A registry key located in the 64 bit portion of the
HKEY_CLASSES_ROOT key, in 64 bits Windows versions.
HKCR32:
A registry key located in the 32 bit portion of the
HKEY_CLASSES_ROOT key, in 64 bits Windows versions.
For 32 bits Windows versions, HKLM and HKCR are used instead. Specific value names or data parts to remove are specified in the lines below the key's line.
In the scan log, all reported items contain an extra line telling the item's check state when the scan completed.
Removal logs thell the result of the removal/repair operation for each item.
Custom Scan
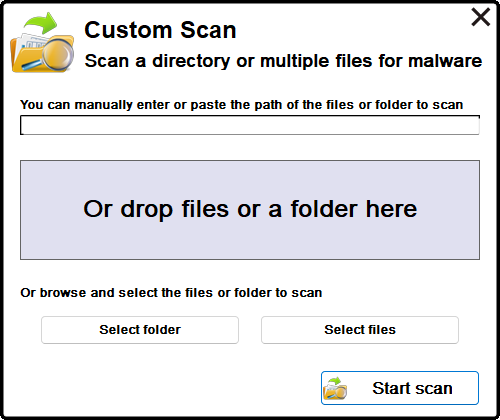
Threat Scanner's Custom scan is very dinamic and lets you easily select the items to scan. You can manually enter or paste the path of the file or folder you wish to scan in the taxt field near the top of the dialog box.
You can also drop the desired files or folder in the gray box, to automatically select them for scanning.
Additionally, you can also use the Select folder or the Select files buttons to indicate the items you want to scan.
You can only indicate one folder, but you can select several files.
Once you have indicated the desired files or folder, press the Start scan button. Threat scanner will start scanning the file objects you have indicated, and display infected files found in the Malware tab.
The removal of the infected files is identical to a normal scan
Other options
Click the Online help (F1) link whenever you want to come back to this page.
Click the Home link if you want to go back th the UVK's Home section.
